
by Elena Planas | Dec 5, 2023 | (meta)modeling, AI, article, Model-driven Engineering, security
Access-control is a key element to manage security in any user interface. This is the first attempt to extend conversational user interfaces with access-control capabilities.
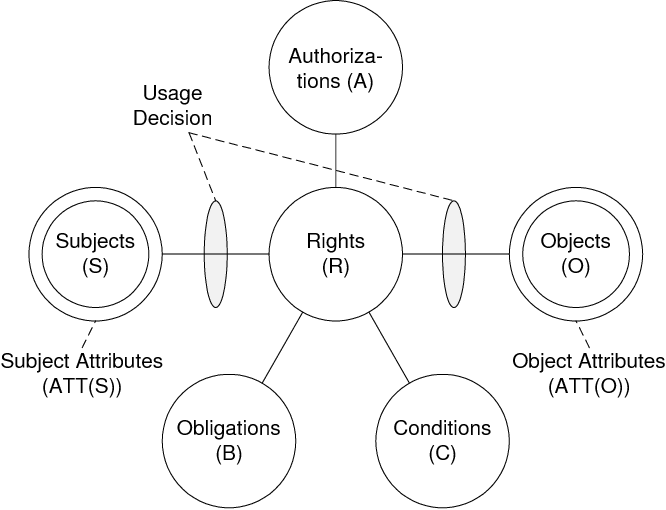
by Jordi Cabot | Jan 4, 2022 | article, DSLs, security
Model powerful security policies for your software designs with our DSL based on the UCON usage control model
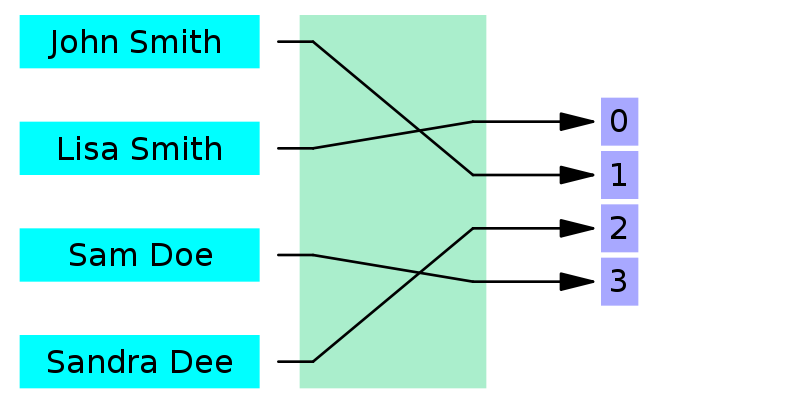
by Salvador Martínez | Aug 9, 2021 | article, security
We present a novel robust hashing mechanism for models. Robust hashing algorithms (i.e. hashing algorithms that generate similar outputs from similar input data) are useful as a key building block in intellectual property protection, authenticity assessment and fast comparison and retrieval solutions

by Johannes Geismann | Nov 17, 2020 | security
Model-driven development has become a leading paradigm for developing CPS because it enables the developer to verify safety requirements in early development phases and refine the models into an implementation preserving the verified requirements.

by Salvador Martínez | Apr 30, 2020 | security, event, Model-driven Engineering
Second edition of our workshop exploring the mutual benefits of combining model-driven engineering and security techniques.

by Salvador Martínez | Apr 8, 2019 | article, security
An initial roadmap towards the holistic protection of intellectual property (IP) in collaborative modeling scenarios based on the adaptation of Cryptography, Access-control and Digital Rights Management mechanisms








Recent Comments