Some weeks ago we prepared a short survey about security aspects in Java-based web applications. We got 41 answers that allowed us to shed some lights on 1) the importance of security aspects according to Java web developers 2) how they define and use the access-control mechanisms to manage them 3) the main security properties they consider when doing it. You can find the full data of the responses at the following link. For a summary of the main conclusions we can draw from the data keep reading!
Importance of specifying security (access-control) aspects in Java web applications
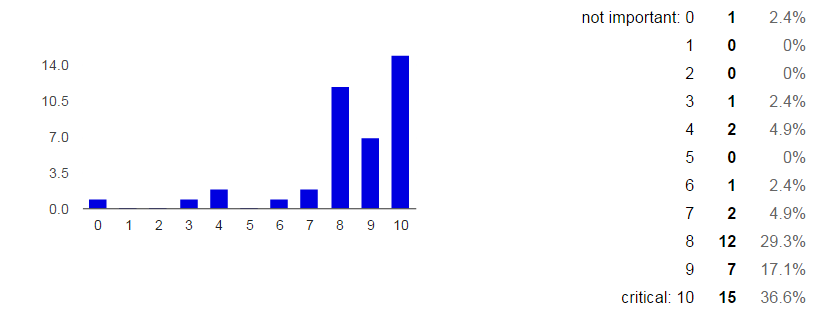
88% of developers consider security aspects critical during the development of web applications Click To Tweet 78% of developers define access-control policies as part of the creation of a web application Click To Tweet Over 40% of developers have witnessed security leaks due to access-control policy misconfigurations Click To TweetHow security aspects are defined?
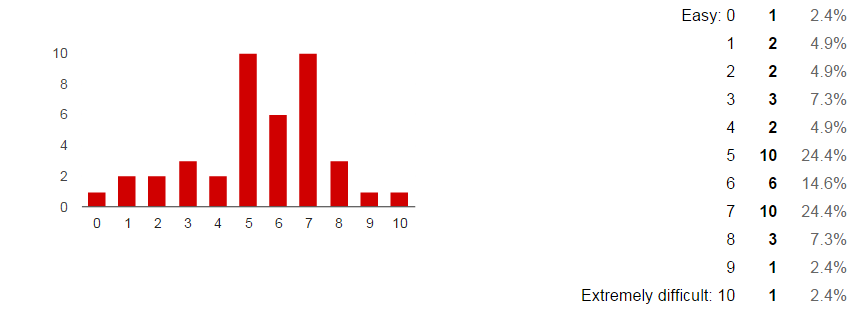
75% of developers feel that defining access-control policies is challenging and would appreciate tool support Click To TweetAccess-control is very often implemented using the deployment descriptor, direct calls to the security Java EE API and other security frameworks beyond Java EE. On the other hand, code annotations are scarcely used. In particlar 68% respondents either never or rarely used it.
Java developers hardly ever use code annotations to express security constraints Click To TweetWhat security properties are more relevant?
Among the different risks that could affect a Java-based web application, having private resources involutarily exposed (reachability) and access-control policies accidentally hiding other ones (shadowing) are perceived as really important by around 93% (38/41) and 83% (34/41) responders respectively.
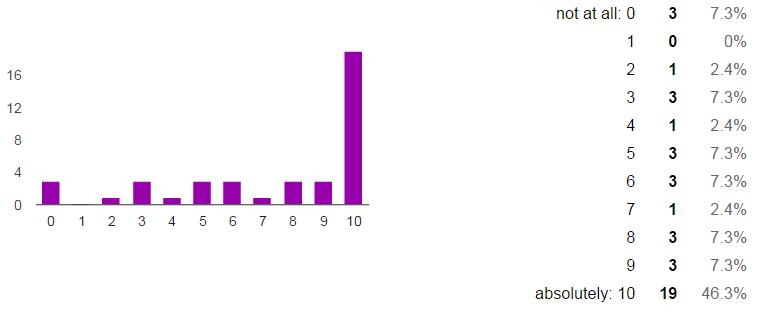
Most critical security risk for devs are exposing private resources and shadowing public ones Click To TweetOn the other hand, having reduntant access-control policies (redundancy) does not entail a big security risks for more than 51% (21/41) of the respondents. However, around a large majority of the respondents think that reachability (66%), shadowing (63%) and redundancy (68%) are security properties that are likely to be violated while putting in place an access-control policy.
These results point out that the definition of security policies is perceived as an important activity by developers, but at the same time it is complex and error prone. Thus, a tool could be come in handy to help Java EE developers setting up error-safe security policies. We’re working on it!
We're working on a tool to automatically detect security risks in Java web applications. Interested? Click To TweetI’m Valerio Cosentino, a postdoctoral fellow in the SOM Research Lab at IN3 UOC, in Barcelona, Spain. My research interests are mainly focused on source code analysis, Model-Driven Engineering (MDE) and Model-Driven Reverse Engineering (MDRE). In the last years, I have been working on the analysis of OSS projects and their communities.




Recent Comments