(work presented at MDsec’12 co-authored with Salvador Martínez, Joaquin García-Alfaro, Frédéric Cuppens, Nora Cuppens-Boulahia and myself).
Network security policies constitute a critical concern when developing and maintaining corporate information systems. Among them, access-control policies present, due its relative simplicity, an special interest. These policies indicate which subjects are allowed to interact with a given object. In the networking environment, they indicate which hosts can send, under given conditions (i.e., which protocol or port is used, etc) , messages to other hosts. In this context, firewalls, designed to filter the traffic of a network with respect to a given number of filtering rules, are key elements in the enforcement of security policies.
However, the implementation of such policies by firewalls remains a very complex (the policy is generally implemented by using low-level languages and may be distributed among several elements) and error-prone task, so that differences between the implemented policy and the desired one may arise.
Accordingly, once implemented, knowing which access control policy is actually being enforced by the firewalls in the network system is a complex and time consuming task that requires, low-level and vendor-specific expertise. Given a network system consisting in several firewalls configured with hundreds of rules (in big companies, having up to one thousand firewalls is common practice), the feasibility of this manual approach could be seriously questioned. As a consequence, in an always-evolving context, where security policies are often updated to respond to new security requirements, this policy discovering task becomes critical as it could hamper the proper evolution of the system and compromise its security.
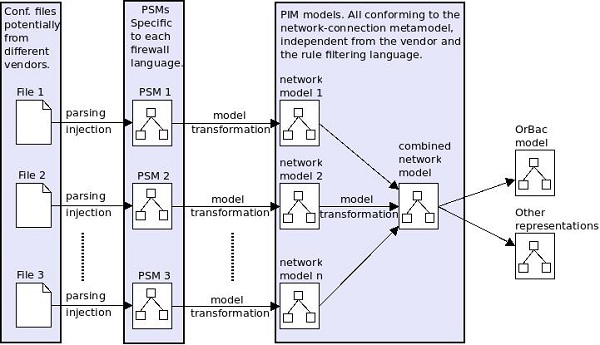
To tackle this problem. we propose a model-driven approach aimed at extracting a model of the access control policy enforced by the firewalls within a network system. Our approach produces a model that abstracts the information from the low-level firewall configurations so that knowing the specificities of a concrete system is not longer needed to understand which access control policy is being implemented.
The approach consists in the following steps:
- Parsing/injecting firewall configuration files into platform specific models (PSMs).
- Transforming the obtained PSMs into Platform independent models (PIMs), conforming to a metamodel able to represent network access-control policies.
- Aggregating the individual PIM models (all conforming to the same metamodel) into a global model conforming to the same metamodel.
- Additionally, a further step aiming to reach formalisms focused in general access control and not network access-control can be performed by transforming the aggregated model into access-control models like RBAC and OrBac.
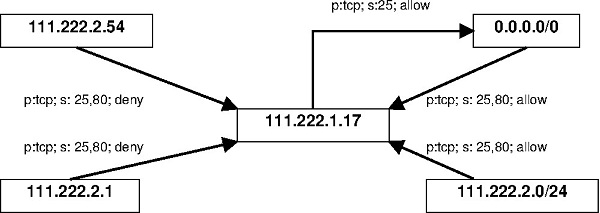
Once this model is available, reasoning about the policy implemented on the network is accessible for non-technical security experts. Moreover, a plethora of Model Driven Development (MDD) tools, like query engines, graphic editors, etc., will become automatically available.
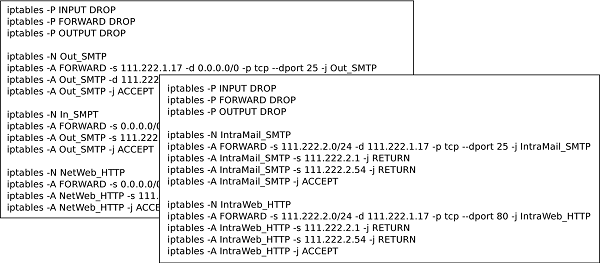
As an example of the capabilities of our approach, we show the model extracted from two configuration files (We show only the rules corresponding to two services, HTTP and SMPT) corresponding to two firewalls in a network composed by a public host, a DMZ (demilitarized zone) and a private network.
As we can see, the task of extracting the global access control policy enforced by the set of rules in these two firewalls (that are just minimal excerpts of what a full configuration policy would be) requires expert knowledge about netfilter iptables. Its syntax along with its execution semantics would have to be mastered to properly interpret the meaning of the configuration files. Moreover, the information from the two configuration files and the global policy for the default iptables chains would have to be combined as they collaborate to enforce the global policy and can not be regarded as isolated.
Conversely, our approach automatically provides to the user a model showing the access-control policy enforced by the system, abstracting the low-level and topology details so that it is easier to understand and manipulate than the original configuration files.
FNR Pearl Chair. Head of the Software Engineering RDI Unit at LIST. Affiliate Professor at University of Luxembourg. More about me.



Recent Comments